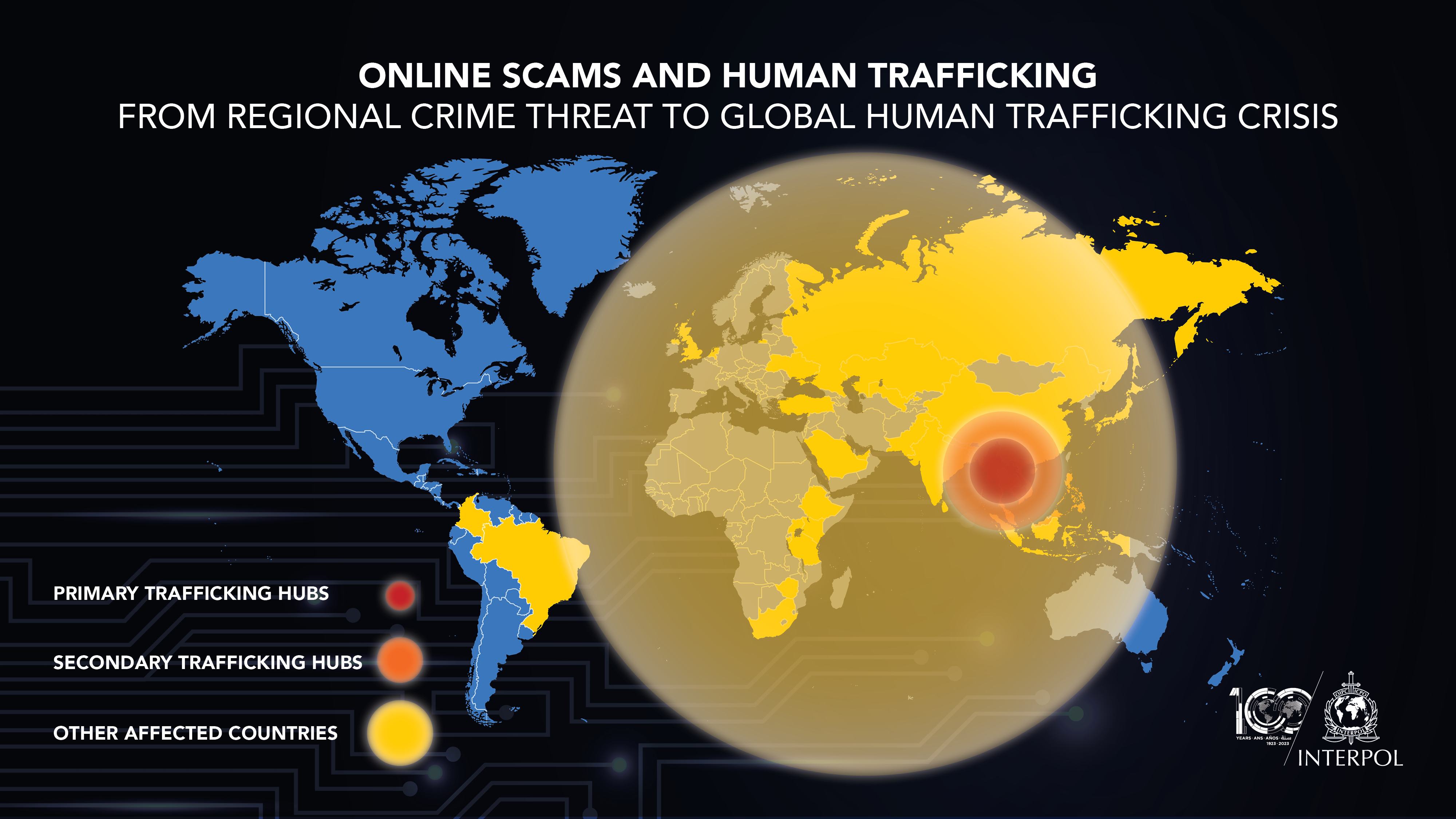
Overview: The Brianna Aguilera Case and Its Broader Implications
The recent discussion surrounding the death of Texas A&M student Brianna Aguilera has sparked considerable public debate. In a widely viewed Court TV appearance, defense attorney Josh Kolsrud explained why the Austin Police Department reached a conclusion of suicide. His comments have fueled conversations regarding police methods and the public’s trust in investigative processes. This opinion editorial takes a closer look at the case, examining how police weigh evidence, the role of prior statements and phone notes, and the tension between zealous family representation and the objective pursuit of facts. By analyzing these elements, we can better understand how law enforcement and legal professionals figure a path through the tangled issues inherent in high-profile investigations.
Police Methods and the Tricky Parts of Investigative Evidence
One of the key focal points in the Aguilera case is the way in which evidence is evaluated during a police investigation. In his commentary, attorney Kolsrud emphasized the significance of repeated suicidal declarations as reported by multiple sources. When investigators report that a decedent expressed suicidal thoughts on more than one occasion, it can sometimes be a crucial piece in forming a clear picture of intent and mental state. However, it is important to recognize that not all evidence is cut and dry; there are a number of tricky parts and confusing bits in determining whether a death is self-inflicted or the result of possible foul play.
Police typically rely on the following essential indicators when forming their conclusions:
- Repeated statements of self-harm and suicidal ideation
- Physical evidence, such as a note expressing intent
- Absence of defensive wounds or signs of a struggle
- Overall mental and emotional context of the decedent
Advantages in using these elements include the ability to construct a timeline of events and to gather corroborative evidence from multiple sources. However, the system is also riddled with tension as each point can often be subjected to interpretation. For instance, if a decedent’s repeated mentions of suicide are taken out of context, or if a phone note is misinterpreted, it can lead to an investigation that may miss small distinctions or subtle details. What is critical is ensuring that each piece of evidence is not only recorded but also corroborated by additional facts.
Understanding the Evidence: The Role of Phone Notes and Prior Suicidal Comments
One of the more contentious points in the Aguilera investigation is the phone note reportedly found on her device. According to reports, this note may have contained explicit sentiments explaining her desire to end her life. From the police’s perspective, if the note is genuine and unquestionably attributable to Aguilera, it serves as super important evidence in supporting the conclusion of suicide.
When we take a closer look at this element of evidence, several key observations emerge:
- Reliability: Authenticity and attribution of the note are non-negotiable. Establishing that the note was indeed written by Aguilera is a chief concern, as its forensic analysis might also reveal hidden complexities regarding the context in which it was written.
- Repetition is Key: Police reports indicate that Aguilera made multiple statements about her suicidal thoughts in October. Repeated declarations carry more weight than a single, isolated comment because they suggest that her mindset was consistently troubled over a period of time.
- Context Matters: The note must be viewed in conjunction with other pieces of evidence, such as her behavioral patterns, the scene of the death, and reports of her mental health state. Factors like heavy alcohol consumption and emotional instability serve to reinforce the interpretation presented by law enforcement.
Each of these points is emblematic of the challenges faced by investigators. While on the one hand, such evidence can offer a compelling narrative supporting a suicide conclusion, on the other, it remains critical to consider whether these individual pieces can be conclusively linked to a singular outcome without ambiguity.
Exploring the Absence of Defensive Wounds and Signs of Struggle
An essential part of police investigations in cases that could suggest foul play is the physical evidence gathered at the scene. In Aguilera’s case, reports indicate that there were no defensive wounds or marks indicative of a struggle. According to Kolsrud, the absence of such findings makes it significantly tougher for police to develop a criminal theory postulating that another person was involved in her death.
This aspect of forensic evidence highlights several issues:
- Physical Clues: In many violent scenarios, one would expect to encounter clear signs of a physical altercation. The absence of such indicators can steer the investigation towards accepting a self-inflicted outcome as more plausible.
- Rule-Out Factors: The lack of defensive wounds acts as a crucial rule-out point. Investigators rely on physical evidence to either confirm or contradict witness statements and other documented evidence.
- Alternative Theories: It is important to consider that while the absence of signs of struggle lends credence to a suicide finding, it does not entirely eliminate all suspicions of external involvement. Some might argue that a victim left alone without a struggle could have been overpowered or had trouble putting up any resistance.
The role of physical evidence, such as the absence of defensive injuries, thus becomes a critical factor. It allows police to bypass some of the tangled issues that can often derail an investigation into suspicious deaths. Nonetheless, it is also important to remind ourselves that every investigation contains its own set of complicated pieces that require cautious evaluation.
Assessing Motive and Opportunity in the Context of the Aguilera Investigation
Another central theme in the race to determine the manner of Aguilera’s death is the absence of clearly identifiable motive or opportunity for any potential assailant. Law enforcement officials consider these factors essential when exploring whether a death might be a homicide rather than suicide.
In many criminal investigations, motive and opportunity are pillars that support the broader conclusion. Here’s how these elements are weighed in the context of the Aguilera investigation:
- Motive Analysis: When a person is believed to have taken their own life, establishing that there was no external influence can help solidify the conclusion. In Aguilera’s case, police noted that her repeated expressions of distress and despair could be seen as indications that her decisions were driven by her internal struggles, rather than by an external coercive force.
- Opportunity Considerations: The investigation took note that there were no compelling signs or circumstantial evidence that another person was present, which would hint at foul play. Without the physical or circumstantial context highlighting external involvement, it becomes more daunting for critics to challenge a conclusion of suicide.
- Interrelated Factors: Motive and opportunity are closely intertwined with other elements of the case, including the phone note and the behavioral context. When all of these pieces are put together, they often provide a cohesive narrative. However, this process is definitely loaded with tension, since even small twists or discrepancies might alter the overall conclusion.
This part of the debate emphasizes how the absence of an external actor’s motive and the lack of opportunity for an assailant can contribute to reinforcing a police theory that leans towards suicide. Yet, some might point out that even in cases where motive and opportunity seem to be missing, certain investigations may still reopen with new forensic findings. This delicate balance between available evidence and the possibility of unexplored avenues is one of the nerve-racking aspects of any criminal investigation.
The Battle Between Family Advocacy and Law Enforcement Reporting
Attorney Josh Kolsrud made an interesting point when he commented on how the advocacy of the family’s lawyer is sometimes seen as purely a way to earn a paycheck or to push back strongly against the police’s findings. In many high-profile cases, the tension between grief-driven family advocacy and the technical analysis of law enforcement can lead to a public perception that is as divided as it is passionate.
There are several reasons why this balance is so loaded with problems:
- The Emotional Factor: Lawyers representing grieving families are under immense pressure to question every aspect of the investigation. Their involvement is often seen as a necessary check and balance to ensure that no hidden complexities are ignored. However, when their arguments are perceived as overly aggressive or driven solely by emotion, they can sometimes be dismissed as lacking objective analysis.
- Objective Versus Subjective Evidence: While law enforcement relies on objective data and forensic evidence to build its case, family attorneys may prioritize circumstantial and testimonial evidence. This divergence can lead to a scenario where the same set of facts is interpreted through widely different lenses.
- Public Perception and Media Coverage: In the age of social media and round-the-clock news, narratives can quickly become polarized. The media’s role in amplifying every minor twist can lead to an environment in which even small distinctions in testimony are blown out of proportion. This public scrutiny adds a layer of complexity that legal professionals must navigate carefully.
The interplay between advocacy and evidence reminds us that while emotional appeals are completely understandable, they must always be weighed against the available facts. The challenge for legal experts is to ensure that no single element—no matter how emotionally charged—overshadows the more technical parts of an investigation.
Re-Evaluating Conclusions: The Importance of a Provisional Verdict
While a conclusion of suicide may appear to be a reasonable interpretation based on the facts presented by police, it is by no means the final word on the matter. Kolsrud’s remarks clearly stated that if future forensic findings or autopsy results reveal inconsistencies with a self-inflicted death, the case should be reopened without hesitation.
This stance underlines some key ideas:
- Provisional Nature of Conclusions: In criminal investigations, conclusions are often provisional and subject to change as new evidence comes to light. This dynamic process ensures that justice remains flexible and responsive to emerging facts.
- Importance of Autopsy Findings: Autopsy results can sometimes uncover subtle details that are not immediately visible at the scene. These fine points may necessitate a closer look and a complete reassessment of the overall findings.
- A Commitment to Transparency: The willingness to revisit and potentially revise an initial conclusion is crucial for maintaining public trust in law enforcement. Open-mindedness and a commitment to re-examining the evidence are essential when the stakes are as high as they are in a case like Aguilera’s.
In practical terms, a provisional conclusion compels all involved to stay vigilant and continue gathering fine details. It means that the investigation is never truly closed, but rather, it remains an evolving record of forensic and testimonial input. Such a stance not only safeguards the integrity of the legal process but also serves as a critical reminder that in the world of criminal investigations, no verdict should be considered set in stone.
Analyzing the Police Approach: Balancing Evidence with Public Perception
The methodology employed by the Austin Police Department in this case reflects a broader approach commonly used in homicide and suicide investigations. By critically examining the absence of physical confrontation markers and piecing together the repeated emotional expressions of despair, law enforcement agencies strive to build what they consider a logically coherent case. However, this approach does not come without its own set of tricky parts.
Key aspects of the police approach include:
- Weighing Verifiable Facts Over Speculation: The police are tasked with sorting out the objective testimony from the subjective narrative. By emphasizing repeatedly recorded suicidal statements and tangible evidence like phone notes, they aim to make their argument as bulletproof as possible.
- Reconciling Public Opinion: The media and public often focus on what is missing—a struggle, defensive wounds, or even a clear motive for homicide. Without these, the public might believe that the investigation is superficial. In reality, however, the absence of such evidence can be as telling as its presence.
- Openness to Re-Evaluation: As discussed earlier, the police themselves have indicated that should autopsy results or newly discovered forensic evidence point to a different cause of death, the investigation will be revisited. This keeps the process transparent and ensures that no detail—no matter how minor—is overlooked.
This approach, while systematic, also highlights the challenge of maintaining public trust. When families and advocates feel that the initial conclusion was reached too quickly or without sufficient consideration of every possibility, it can lead to significant public outcry. Therefore, balancing the need for a decisive conclusion with the openness to new evidence is a delicate dance that law enforcement must perform.
Critical Analysis of the Evidence: Weighing the Pros and Cons
Looking closely at the fine points of evidence in the Aguilera case, it becomes apparent that there are both strong arguments in support of and against the suicide conclusion. For those invested in ensuring that every twist and turn of the case is examined, the following table summarizes the key pros and cons observed in this investigation:
| Aspect | Supporting Evidence for Suicide | Points of Contention |
|---|---|---|
| Prior Suicidal Statements | Multiple recorded expressions of despair suggest a gradual buildup of intent. | Contextual factors, such as the influence of external stressors, remain open to interpretation. |
| Phone Note Evidence | An allegedly authentic note could provide a direct expression of intent. | The authenticity and authorship of the note need rigorous forensic verification. |
| Absence of Defensive Wounds | Lack of physical struggle indicators supports a scenario with no external assailant. | Some argue that an absence might not completely rule out all forms of external involvement. |
| Motive and Opportunity | The elimination of clear external motive or opportunity points to self-infliction. | The potential for overlooked evidence highlighting a hidden external actor cannot be discounted. |
Such a table not only brings to light the different layers of evidence but also helps in identifying where future investigations might need to poke around for additional clarity. It is through this methodical breakdown that both supporters and skeptics of the suicide conclusion can better understand the reasoning behind the police’s determination—and where they might disagree.
Legal Perspectives: Balancing Advocacy and Objective Analysis
The manner in which legal professionals approach cases, like that of Aguilera, often reflects a dual commitment to both objective fact-finding and zealous advocacy for their clients. With cases that are loaded with emotional nuance, lawyers on both sides must tread carefully between supporting the evidence at hand and ensuring that every potential detail is unearthed.
Important aspects of this legal balancing act include:
- Objective Analysis: Law enforcement and independent forensic experts rely on measurable and repeatable data. This includes everything from toxicology reports to the analysis of digital footprints on devices like cell phones.
- Advocacy for Affected Parties: Family attorneys play a keystone role in challenging established narratives if they believe that key details have been overlooked or misinterpreted. Their role is intrinsically linked to ensuring that every subtle part of the investigation is reviewed.
- The Intersection of Emotion and Evidence: Cases involving loss, especially in such emotionally charged scenarios, often reveal a stark contrast between what the evidence seems to imply and the feelings of those left behind. Balancing these perspectives requires both legal acumen and an empathetic approach.
It is important to note that a case such as Aguilera’s not only tests the skills of forensic investigators but also the ability of legal professionals to manage public sentiment. In many ways, this conflict between advocacy and the reliance on objective data encapsulates the broader challenges facing the legal community today.
Dealing with the Overwhelming Issues: Public Perception and Media Narratives
As news outlets and social media continue to cover cases like Aguilera’s extensively, public perception often becomes as much a part of the story as the physical evidence itself. The influence of media narratives can sometimes obscure the fine details of an investigation, leading to a scenario in which emotional storytelling competes with the harder, more technical reports from law enforcement.
Several factors contribute to this phenomenon:
- Simplification of Complex Evidence: In the realm of public reporting, it is common to see complicated pieces of evidence simplified into catch-all statements. This sometimes results in distorted views where the full context is lost.
- Emphasis on Emotional Appeals: Stories that delved into the human aspects of a case, such as personal testimonies and heartfelt family statements, often gain traction in the media, even if they do not provide the full forensic picture.
- Framing the Narrative: The way in which police conclusions are presented—especially if they appear to contrast with the family’s perspective—can lead to polarized opinions. In such scenarios, the careful balance between factual reporting and emotional narratives requires constant managing of public expectations.
In response to these challenges, it is crucial for legal professionals and law enforcement to maintain transparency throughout the investigative process. By openly discussing the evidence and its interpretation, authorities can help the public understand that investigations are fluid and that every piece of data—even if it seems overwhelming at first—will be carefully considered.
Lessons for the Legal Community: Finding Your Path Through Tangled Issues
The Aguilera case, with all of its twists and turns, offers several key lessons for the legal community at large. At its core, this case encapsulates the need to get into the nitty-gritty of every detail, ensuring that all subtle parts are weighed fairly before arriving at a conclusion.
Some of the super important lessons that attorneys, investigators, and the public can take from this case include:
-
The Importance of Thorough Documentation:
Every statement, note, and piece of physical evidence must be meticulously documented. This is critical for building a coherent narrative that can stand up to scrutiny in legal settings.
-
Openness to New Evidence:
As forensic methods evolve, what might have been considered conclusive at one stage of an investigation can later be reevaluated with more sophisticated technologies. It is vital that investigators remain ready to reconsider previous findings if new clues emerge.
-
Collaboration Across Disciplines:
The collaboration between law enforcement, forensic experts, and legal professionals is key. A combined effort often uncovers little details that might otherwise be missed if each entity operated in isolation.
-
Balancing Advocacy and Factual Analysis:
Legal advocates must always ensure that their arguments are grounded in verifiable facts. While emotional appeals are natural, especially in cases involving loss and tragedy, they must not override a rational evaluation of all available evidence.
These lessons serve as a reminder that legal practice is not simply about defending or prosecuting, but about ensuring that the truth is revealed—even when that truth is wrapped in tangled issues and nerve-racking uncertainties.
Reflections on the Dynamic Nature of Criminal Investigations
Criminal investigations, particularly those involving high-profile cases, are rarely straightforward. The Aguilera case illustrates that each investigation is filled with twists and turns that require continuous re-examination. While the current evidence may support a conclusion of suicide, the investigative process does not end there. It remains an evolving exploration where new forensic details have the potential to completely alter the understanding of events.
This dynamic nature is evident in how law enforcement approaches each new piece of evidence:
- Reevaluation Process:
If corroborative findings suggest that the current narrative does not fully capture the reality, investigators are prepared to re-open the case. This ensures that every potential angle is considered before a final verdict is reached.
- Continuous Learning:
Every high-profile case contributes to a broader pool of knowledge. Lessons learned from earlier investigations guide investigators in managing the confusing bits of new cases, helping them to better figure a path through similar challenges in the future.
- Public Communication:
Maintaining open lines of communication with the public is crucial. When authorities explain the reasoning behind provisional findings, it fosters trust and ensures that the community remains informed about the investigative process.
In this way, the policing of complex fatalities becomes less about a single moment of conclusion and more about a rigorous, ongoing evaluation of every single part of the evidence. While this process may seem intimidating or off-putting at times, it ultimately lends strength and credibility to the legal processes that govern society.
Looking Ahead: The Future of Investigative Transparency and Public Trust
Given the critical nature of cases like that of Brianna Aguilera, the future of investigative transparency is an issue that deserves our full attention. Police departments and legal institutions must work together to ensure that their methods for assessing evidence continue to evolve and that public trust is maintained through clear, open communication.
Some key strategies moving forward include:
- Enhanced Forensic Technologies:
Investing in modern forensic analysis can help illuminate the fine points of each investigation. More accurate data can lead to earlier identification of discrepancies and better overall evaluations.
- Regular Public Updates:
By briefing the community on how evidence is reviewed and integrated into the broader narrative, law enforcement can help reduce the nerve-racking uncertainty that often surrounds high-profile investigations.
- Collaboration with Independent Experts:
Partnering with external forensic and legal experts can provide additional layers of scrutiny. This collaborative strategy not only strengthens the case but also bolsters public confidence in the investigated outcomes.
- Structured Oversight:
Implementing oversight mechanisms that monitor the entire investigative process can help ensure that every piece of evidence is critically examined without bias, thereby improving both internal accountability and public transparency.
Ultimately, when the processes behind investigations are visible and continuously refined, it becomes easier for both legal professionals and the public to work through the tangled issues that arise in such cases. This is not just beneficial for uncovering the truth behind any single case, but is also super important for strengthening the integrity of the legal system as a whole.
Conclusion: A Balanced Look at a Case Under Continuous Scrutiny
The Brianna Aguilera investigation continues to be a topic on which expert opinions and public sentiments diverge. While defense attorney Josh Kolsrud asserts that the available evidence—ranging from phone notes and repeated suicidal statements to the absence of physical signs of struggle—supports the conclusion of suicide, it is clear that every interpretation of the evidence carries its share of tangled issues and nerve-racking uncertainties.
This opinion editorial has taken a closer look at the investigative process as presented in the Aguilera case, exploring the essential aspects of police methodology, the weighing of objective versus subjective evidence, and the complex interplay between legal advocacy and public sentiment. Through tables outlining key evidence pros and cons, and bulleted lists summarizing critical analysis points, we have seen that effective criminal investigations are never static but always subject to future revision when new details surface.
In an era where every piece of evidence is scrutinized and every narrative is shared widely, the importance of maintaining transparency and remaining open to reassessment cannot be overstated. If new forensic findings suggest that the narrative needs adjustment, the responsible course of action is to re-examine every small aspect of the case with fresh eyes. Only by doing so can justice be truly served, both for the victim’s memory and for the community’s sense of security.
By recognizing the fine details in evidence and balancing the often conflicting perspectives of law enforcement and family advocates, we can work toward a legal process that is both objective and empathetic. Although the current findings in Aguilera’s case lean towards suicide, they remind us that every investigation is a living process—loaded with intricate parts that require both critical analysis and a willingness to adjust as new facts come to light.
At the end of the day, the search for truth is an ongoing quest, one that demands both the determination to dig into every confusing bit and the humility to accept that sometimes additional evidence may change the narrative entirely. It is through this rigorous, transparent, and balanced approach that the public can have confidence in the system—one that is ready to steer through even the most intimidating and nerve-racking challenges with integrity and dedication.
Read more about this topic at https://kolsrudlawoffices.com/brianna-aguilera-death-investigation/
Related articles you might like
Title 18 - CRIMES AND OFFENSES - PA General Assembly
Trial by Google: Judicial Notice in the Information Age